SSH (Secure Shell) is an essential protocol for remote server access, widely used by network administrators and developers for securely connecting to remote systems. Securing SSH access is vital in protecting servers from unauthorized access and potential attacks. In this article, we’ll walk you through various security measures and configurations to enhance your SSH setup, providing your server with an additional layer of security.
Why SSH Security Matters?
SSH is a powerful tool that provides remote access to your systems over an unsecured network. However, improper configuration or weak security practices can expose your system to brute-force attacks and other cyber threats. By securing SSH, you can mitigate the risk of unauthorized access, password attempts, and intrusion attempts.
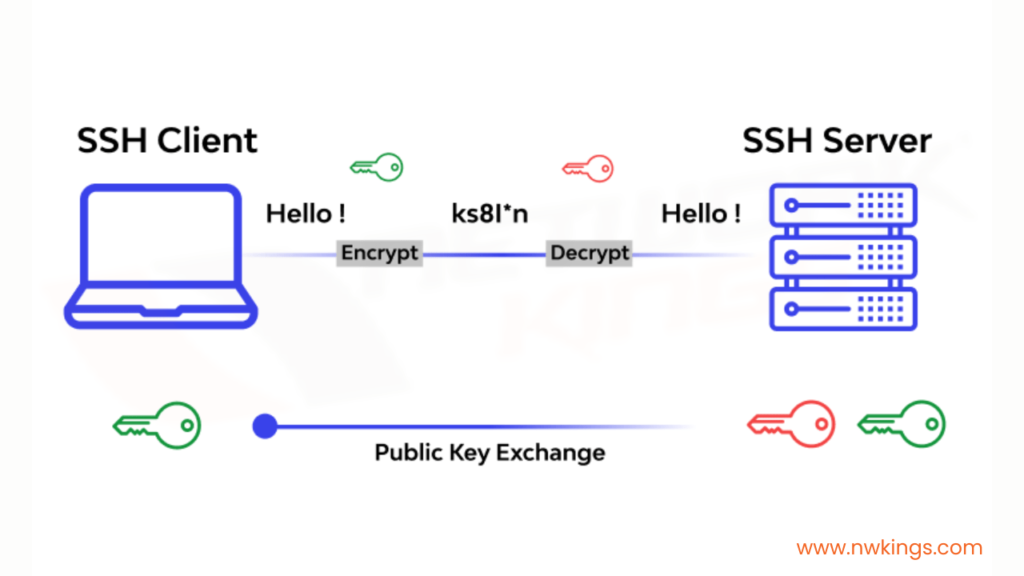
Default SSH Port Vulnerability
By default, SSH operates on Port 22, making it a prime target for attackers. Leaving the default port unchanged increases your system's attack surface. A common security practice is to change the SSH port to a non-standard port, minimizing casual scans and brute-force attempts.
To change the port, you can modify the SSH configuration file:
|
bash sudo nano /etc/ssh/sshd_config |
Look for the line that says Port 22 and change it to your desired port, for example, Port 33001. After saving the changes, restart the SSHD service:
|
bash sudo service sshd restart |
This simple step provides a basic layer of security that makes it harder for potential attackers to identify your SSH service.
Use Key-Based Authentication
One of the most effective ways to secure SSH access is by using key-based authentication instead of traditional password-based authentication methods. Key-based authentication uses a pair of cryptographic keys (a public and a private key) to authenticate users, significantly reducing the risk of brute-force attacks.
Here’s how to set up SSH key-based authentication:
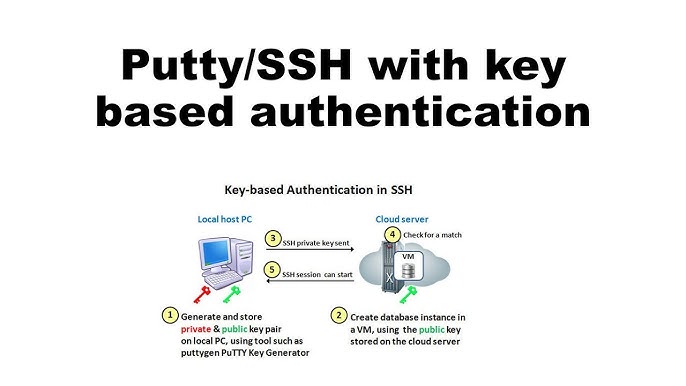
- Generate SSH Keys: Use the following command to generate a key pair:
|
bash |
- Copy the Public Key to the Remote Server: Use the ssh-copy-id command to copy your public key to the remote server:
|
bash |
This method ensures that even if an attacker has your IP address, they cannot access the server without the correct private key. Additionally, consider disabling password-based logins in your SSH configuration file by setting PasswordAuthentication no for further security.
Disable Root Login
Another crucial security measure is to disable root logins. Logging in as the root user poses a significant security risk, as attackers often target the root account with brute-force SSH attacks. To disable root login, modify the SSH configuration file:
|
bash sudo nano /etc/ssh/sshd_config |
Find the line PermitRootLogin yes and change it to PermitRootLogin no. This prevents direct login as root, forcing users to log in as a regular user and then use sudo to execute commands with root privileges. After editing the configuration file, restart the SSH service:
|
bash sudo service sshd restart |
Disabling root access adds an extra layer of protection and minimizes the potential for a security breach.
Implement Two-Factor Authentication (2FA)
Enabling two-factor authentication (2FA) provides an additional level of protection for SSH access. With 2FA, even if an attacker gains access to a user’s password, they still need a second form of authentication, such as a time-based one-time password (TOTP), to log in.
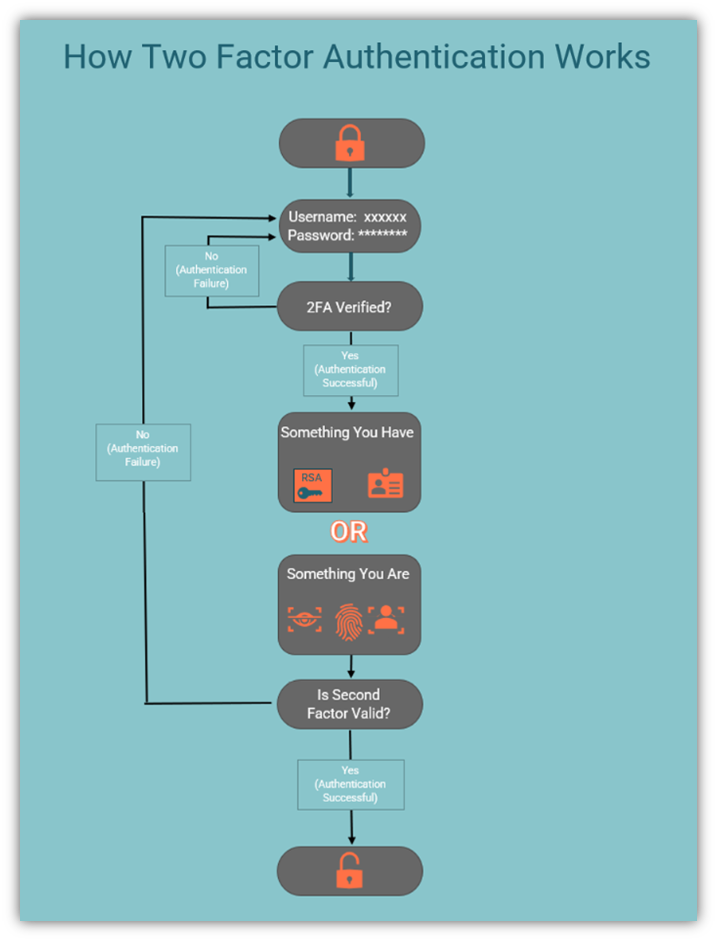
To set up 2FA for SSH, you can install Google Authenticator or a similar 2FA app. Begin by installing the Google Authenticator package:
|
bash sudo apt-get install libpam-google-authenticator |
Once installed, configure it for each user by running google-authenticator and following the prompts. Then, enable 2FA in the SSH configuration by adding the following line to your /etc/pam.d/sshd file:
|
bash auth required pam_google_authenticator.so |
This setup adds a strong authentication mechanism to your SSH service, reducing the likelihood of security breaches.
Limit SSH Access by IP Address
For added security, you can restrict SSH access to specific IP addresses. This is especially useful for remote employees or teams working from particular locations. By limiting access to trusted IPs, you reduce the risk of unauthorized access from potential attackers. To configure this, you can use firewall rules or edit the /etc/hosts.allow and /etc/hosts.deny files. For example, to allow SSH connections only from a specific IP address, add the following line to /etc/hosts.allow:
|
bash sshd: 192.168.1.100 |
And deny all others by adding this line to /etc/hosts.deny:
|
bash sshd: ALL |
These restrictions enhance the security of your remote server and make it difficult for malicious actors to access your system.
Use a Firewall to Secure SSH
A firewall provides an essential layer of protection for any server. By controlling incoming and outgoing connections, a firewall can limit exposure to unwanted traffic and brute-force attacks. You can use firewall-cmd to configure firewall rules that secure SSH access.
Here are a few useful commands to manage SSH connections with firewall-cmd:
- To allow SSH on a custom port (e.g., 33001):
|
bash firewall-cmd --reload |
- To block incoming SSH traffic from a particular IP:
|
bash firewall-cmd --reload |
Configuring a firewall helps reduce the risk of unauthorised access and secures your remote administration sessions.
Monitor SSH Access and Logs
Finally, regularly monitoring SSH logs is an essential part of maintaining SSH security. Reviewing logs can help you identify suspicious activities, such as repeated password attempts or failed login attempts from unrecognized IPs.
The authentication log file /var/log/auth.log provides a detailed record of all SSH login attempts and can be monitored using commands like grep:
|
bash grep "sshd" /var/log/auth.log |
By proactively monitoring this file, you can detect and respond to potential security issues before they lead to a breach.
Securing SSH access is critical in safeguarding your server from potential threats. By following these steps changing the default port, using key-based authentication, disabling root login, enabling two-factor authentication, and monitoring logs you can significantly reduce the risk of a security breach. At DotsDen, we prioritize server security and offer advanced security features as part of our services to ensure safe and reliable remote access for our clients.

